Industrial networking and security in the process industry
To ensure the stable and reliable operation of all processes and to intervene at an early stage if needed, it is necessary to continuously monitor systems in the process industry. The trend here is towards an open architecture with a modular structure that enables plug-and-play integration.
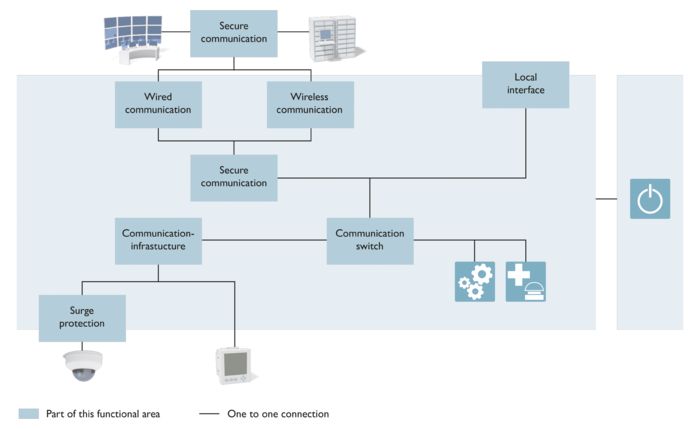
Switches are a central element in industrial communication. They coordinate data between a variety of end devices and enable efficient communication. Unmanaged switches provide standard functionality with a variable number of ports. Managed switches additionally enable traffic analysis and control via redundancy mechanisms and network diagnostics, and have advanced cybersecurity. Routers or 3-layer switches perform similar functions and also enable the connection of subnetworks.
While controller and safety units usually have a direct connection to the switches, some networks require an extended communication infrastructure. Repeaters and extenders increase network performance. Gateways extend the number of devices, and converters integrate devices without an Ethernet interface.
Reliable surge protection is essential for field devices and data lines. The DATATRAB DT product family from the COMPLETE line portfolio is suitable for protecting sensitive data interfaces.
After selecting the suitable switch for the application, other devices, such as monitoring and control components, are connected for the field. Robust panel PCs and HMIs with approvals for potentially explosive areas and maritime conditions are suitable here.
Finally, various subsystems are connected to the higher-level control system via hardwired or wireless solutions. For applications in the local environment, cabling is a simple and reliable solution with fast data transmission. If cabling is not feasible due to long distances, wireless solutions are an alternative. However, these connections are often subject to interference effects such as electromagnetic fields, reflections, fading, interference, and shadowing, which negatively affect data transmission.
A poorly managed or even infiltrated communications infrastructure poses major risks to the stability and security of the network. Therefore, every critical infrastructure application must be protected with IEC 62443 cybersecurity – and at every possible access point wherever possible. With high-performance and flexible firewalls, security routers ensure secure applications in accordance with IEC.









