IEC 62443 – the industrial cybersecurity standard To avoid risks, the international IEC 62443 series of standards defines the security requirements needed for manufacturers, integrators, and operators.

IEC 62443 and ISO 27001 at a glance
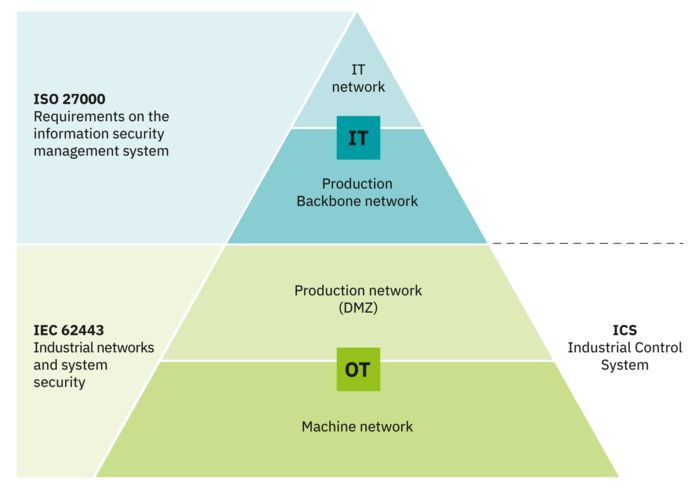
Cybersecurity in IT and OT
Previously, the fields of Information Technology (IT) and Operation Technology (OT) were considered separately and assigned to different specialist departments. However, with the increasing networking and digitalization of systems and productions, these fields are merging into one another. Cybersecurity can therefore no longer be considered in isolation. Only through a coordinated approach can effective and efficient protection against cyberattacks be achieved.
The ISO 27000 series of standards defines protection objectives for IT, with a focus on confidentiality. For the OT field, the availability of systems is crucial, as described in IEC 62443. The IEC 62443 series of standards aims to provide support for the secure operation of industrial automation systems (ICS systems) – from design through implementation to management. To this end, the various standards in the series specify rules for component manufacturers, system integrators, and operators. Component manufacturers must ensure the protection of products, while machine builders and system manufacturers are responsible for their secure interaction. The operator is ultimately responsible for the secure operating processes. IEC 62443 therefore supplements the ISO 27001 standard. Taking both standards into consideration is crucial for holistic protection against cyberattacks.
Structure of IEC 62443
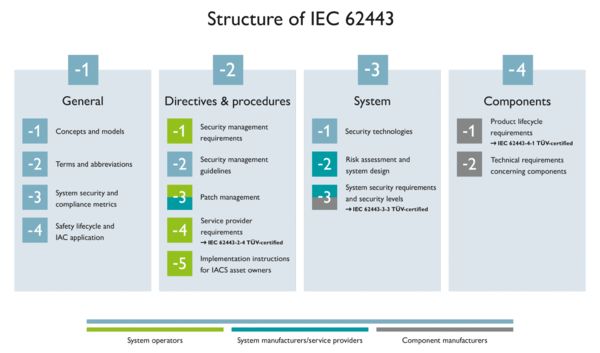
One particular feature of IEC 62443 is the comprehensive security-by-design approach. This includes requirements on operational processes, systems, and on components. In addition, the approach defines both procedural and technical measures.
“Defense in Depth” is a central security concept of the IEC 62443 standard. By stacking several security mechanisms in succession, it is more difficult for attackers to penetrate the system.
Implementation of IEC 62443 as an operator
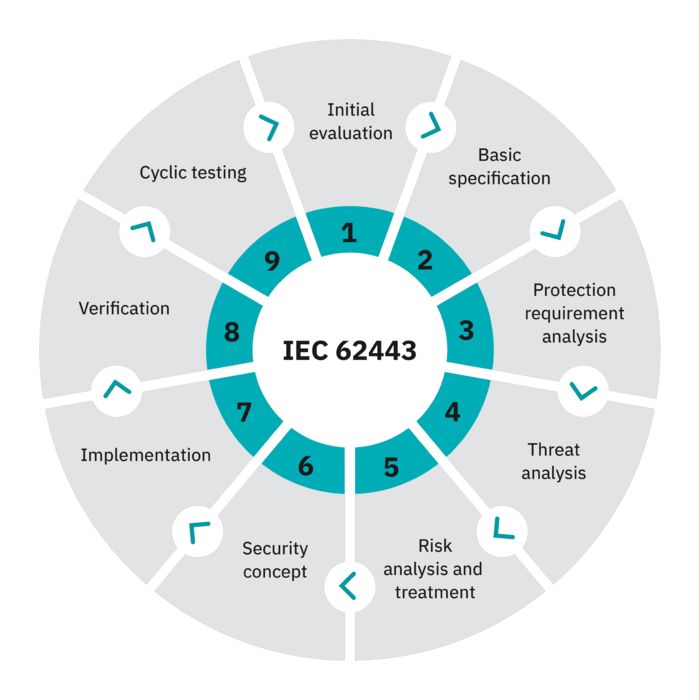
The “Nine steps to a secure system” process.
Developing a secure automation solution begins with defining the assets to be protected. A threat and risk analysis is then performed for each of these. These analyses are then used as the basis for deriving measures for risk reduction and the resulting requirements on the system and the components used.
However, the protection level of a system is not simply determined by its technical capabilities; it is also affected by the processes implemented and the expertise of personnel. A secure system requires permanent monitoring and maintenance. This includes precise knowledge of the installation and its properties, i.e., a network plan and inventory of all components, as well as management of all users, their rights, and their access data.
There is not a single standard solution for all applications. A secure automation solution is always tailored to the individual conditions. The implemented measures must also be checked cyclically and adapted to take the latest state of the art into consideration. As an aid, we have defined the “Nine steps to a secure system” process. This approach enables operators and system integrators to implement security-by-design for their specific solution.
Implementation of IEC 62443 at Phoenix Contact
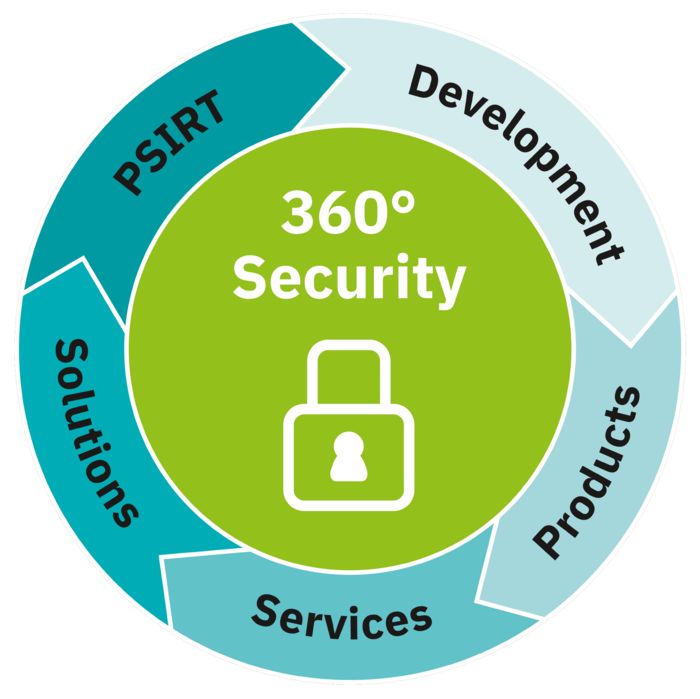
Our comprehensive 360° security concept
360° security concept
Phoenix Contact began implementing IEC 62443 in 2017. However, the protection of systems and facilities can only be guaranteed if they are protected from all sides. For this reason, we have developed and implemented our 360° security concept – a complete range without compromise.
Our approach to cybersecurity is holistic. Each component of our 360° security concept is therefore certified in accordance with IEC 62443. This starts with a secure development process that ensures that our products are equipped with robust security functions right from the start. These security functions are deeply integrated into our products to ensure comprehensive protection. Furthermore, we offer certified services that aim to continuously improve the security of our customers.
Development process certified in accordance with IEC 62443-4-1
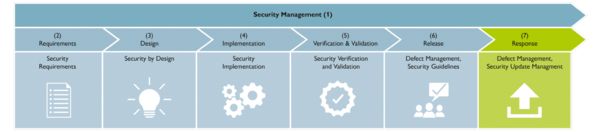
We introduced the secure development process, certified in accordance with IEC 62443-4-1, for our components back in 2018. This process is based on proven cybersecurity principles and defense-in-depth.
Since then, an important part has been transparent and open communication regarding potential security vulnerabilities. To this end, the Product Security Incident Response Team (PSIRT), also certified in accordance with IEC 62443-4-1, publishes reports on potential vulnerabilities and regularly provides security updates for our products.
Products certified in accordance with IEC 62443-4-2
Secure products are developed in accordance with the IEC 62443-4-1 development process and fulfill the functional security requirements of IEC 62443-4-2.
In 2021, PLCnext Control became the first controller to be certified in accordance with the IEC 62443-4-1 ML3 / 4-2 SL2 Feature Set. We now have a two-digit number of products certified in accordance with to IEC 62443-4-2, including the mGuard security routers since the Hannover Messe 2025. Other secure products are currently under development or being certified.
Find out more about our secure products:

Services certified in accordance with IEC 62443-2-4
Services certified in accordance with IEC 62443-2-4
In order to develop, advise on, install, and maintain effective security solutions together with system integrators and operators, the teams involved must have comprehensive cybersecurity capabilities and be able to demonstrate them. Only this will ensure that all security measures meet the highest standards and are implemented effectively.
At Phoenix Contact, the corresponding teams, including those in selected national subsidiaries, are certified in accordance with the international IEC 62443-2-4 standard. This certification confirms that our teams have the necessary expertise and processes to securely integrate and operate industrial automation systems. This qualification means that we can offer our customers worldwide reliable and secure solutions that meet the latest cybersecurity requirements.
Solutions certified in accordance with IEC 62443-3-3
There is no overarching solution for implementing the standards. Rather, you have to implement the rules in accordance with individual needs and circumstances. In order to better explain and implement the process requirements as well as the functional system requirements, we at Phoenix Contact have developed various templates (blueprints) for different markets and solutions.
In addition to the multi-level security strategy (defense-in-depth concept), the “Remote Monitoring and Control” blueprint includes, among other things, the segmentation of zones and conduits, data flow control, end-to-end communication encryption, component hardening, awareness training for employees, and processes for patch management and risk management.
This solution has been certified in accordance with IEC 62443-3-3.
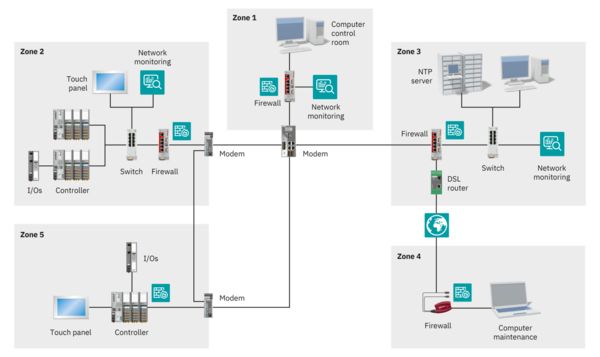
Our “Remote Monitoring and Control” blueprint certified by TÜV Süd in accordance with IEC 62443-3-3
Cybersecurity is becoming law

IEC 62443: Success factor for cybersecurity directives
With the new Cyber Resilience Act (CRA), the new NIS 2 Directive, and the new Machinery Regulation, the implementation of cybersecurity measures in Europe is legally binding. And no longer just for critical infrastructures.
In order to meet the stringent requirements of the new security directives, it is helpful to orient yourself to international standards. One of these standards is the IEC 62443 security standard. For example, IEC 62443 already covers many of the requirements required by the CRA. Both for the secure development process and for technical requirements on products and systems. IEC 62443 is therefore a promising candidate for a future harmonized CRA standard.
The IEC 62443 standard also provides comprehensive assistance for complying with the new NIS 2 security directive and the new Machinery Regulation.

LinkedIn: Industrial communication and cybersecurity Become a part of our community now!
Industrial communication networks enable us to reliably transmit data from the field, through the control level, all the way to the cloud. Our Industrial communication and cybersecurity LinkedIn page provides you with interesting information on network availability, cyber security, remote maintenance, and much more. Become a part of our community!








