Solutions for Industrial Cyber Security What are the differences between IT and OT? IT- Information Technology is a critical layer for a good defense in depth strategy. The main challenge when comparing IT and OT is the priorities. Typically, IT networks prioritize data confidentiality above all else OT- Operation technology utilizes data for some physical result. Therefore, the availability of the data is paramount. In this example people want their systems to keep running and the uptime would be the main measurement of success. This is not to say that securing the data is not important. OT systems also can have protocols allowing for functional safety protecting people from the machines in various way. It is also very common that OT systems run older unsupported software.
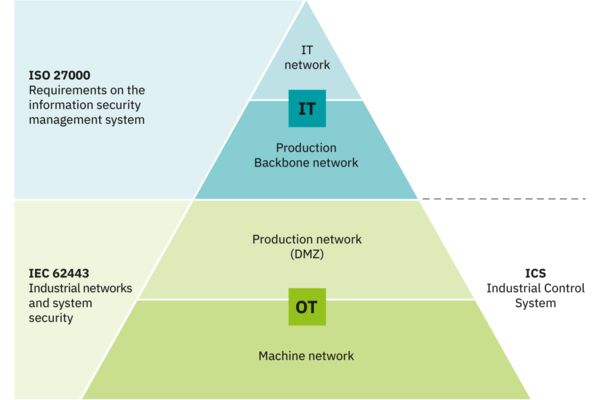
Industrial Demilitarized zone (IDMZ) // Production Network
Industrial Demilitarized zone (IDMZ) // Production Network Creating an IDMZ seen as the Production network is a critical step in creating a secure network allowing isolation for both IT systems and OT systems. Every machine can be isolated and protected by a firewall. At the Production level there can be a redundant network setup to maximize the availability between IT and OT. Typically devices in the machine network will be industrially hardened and have GUI interfaces. Most of the OT technology is designed to be easily replaceable. At Phoenix Contact all of our network switches and routers have an SD card slot and removable terminals so in the event of a hardware challenge the device can be replaced with minimal effort.
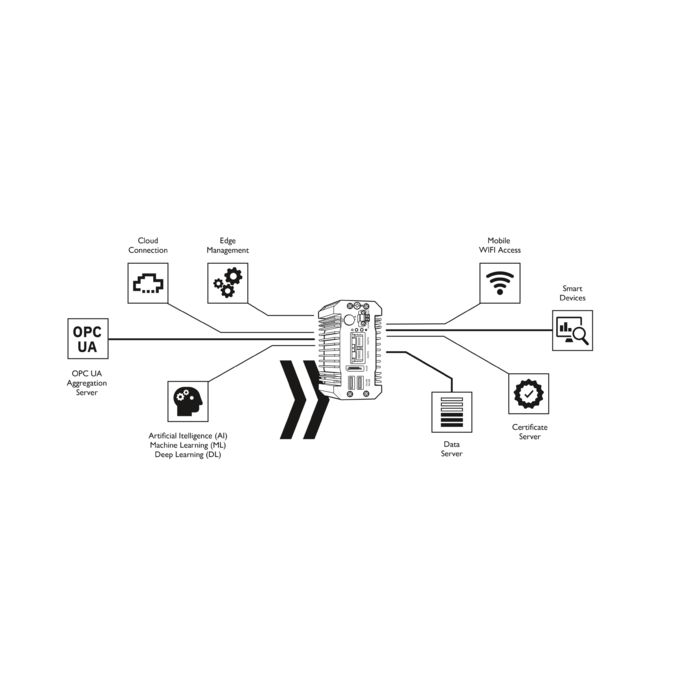
Edge/IoT computing
As the need to connect IT and OT grows the question of how to link these networks is going to be increasingly important. With the IDMZ network setup this is the perfect spot to run an edge gateway. Edge devices are dedicated units that can gather relevant data from specific machines. They then aggregate the data and feed it up into business systems such as ERP systems or dashboards. The benefit of the edge device is that it ensures from a security standpoint that nothing form OT is jumping up two levels in the hierarchy to communicate with IT or vice versa. Because it is in the IDMZ the edge device ensure security for both networks. A single edge device with enough compute can talk to every machine and convert the protocols from a machine level into something tangible for the higher level systems.
Smart edge computing powered by PLCnext Technology. Edge devices from Phoenix Contact are certified for use with Proficloud.io, Cumulocity IoT, AWS Cloud, and Microsoft Azure Cloud.
Your Advantages-
-Security
-Data aggregation
-Local databases
-Protocol conversion
-Better overall network bandwidth

Cybersecurity is the prerequisite for a reliable network
Industrial Cybersecurity
Cybersecurity is the prerequisite for a reliable network
Industrial cybersecurity protects networked industrial systems and plants from attacks, data espionage, failures due to viruses, malware, and misuse. After all, cyberattacks and malware can cause a great deal of damage, from loss of know-how, images, and data to expensive downtime and personnel costs for correcting damage, all the way to high ransom demands.
That’s why we provide security routers and industrial firewalls that are specifically designed to meet the needs of industry and monitor data traffic in the network. Only the data traffic you want is allowed; unauthorized access attempts are blocked. This increases the availability of your systems.
Phoenix Contact offers machine guard units (mGuard) to protect machines from challenges. These are industrial firewalls designed to meet IEC 62443-4-2. Combining this hardware with intelligent managed switches Phoenix Contact is able to help customers from industry create a simple, secure, reliable network.
Brochure- Industrial Cyber Security

FL MGUARD 2100/4300 security routers
With comprehensive security functions, the mGuard security routers protect your industrial network against unauthorized access by people or malware. The proven mGuard security technology enables you to control and safeguard communication within your production network.
Main features
- With the high processing speed, the mGuard security router achieves a data throughput of almost 1,000 Mbps
- Comprehensive security functions such as stateful inspection firewall, Network Address Translation, and Stealth mode
- The central management software, mGuard Device Manager, enables easy and efficient system configuration, maintenance, and operation, especially when a large number of mGuard security routers are installed
Your Advantages
- With the high processing speed of the mGuard security routers, data flow within your network is not slowed down
- High level of security through proven mGuard security technology and over 20 years of experience in cybersecurity
- Long-term software maintenance and high security through timely updates enable many years of use
Concentrator Panel
The concentrator panel system from Phoenix Contact integrates IEC 62443-4-2 certified hardware to effectively isolate IT from OT. This streamlined solution facilitates the transformation from an outdated star topology to a modern layered architecture. Designed to protect IT, OT and also create an industrial demilitarized zone (IDMZ) this is the ideal setup for modern facilities looking to digitalize. Redundancy is a major key to uptime so the solution includes redundant power supplies and managed switches. All devices can be configured using an intuitive graphical user interface (GUI) and have an optional SD card for easy device replacement. Leveraging the PLCnext technology as an edge device allows for secure collection of all relevant signals.
This entire system is backed by Phoenix Contacts Limited Lifetime warranty. Start securing your network today with Phoenix Contacts advanced solutions.

Lifetime Warranty Choose Phoenix Contact with Complete Confidence
Dedication to quality and innovation, united with our strong commitment to provide customer peace-of-mind, form the foundation of this exclusive Phoenix Contact warranty program.

