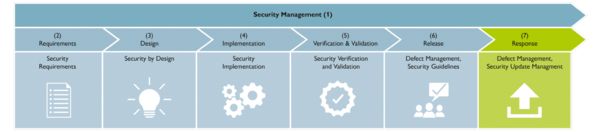
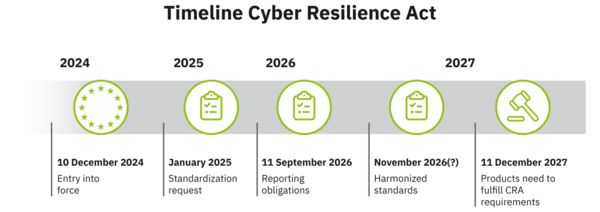
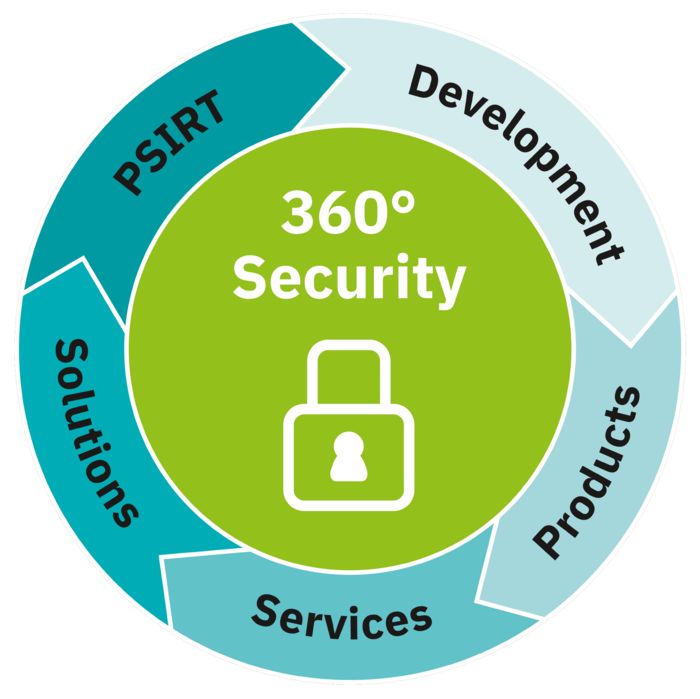
The CRA stipulates clear security requirements for products, including access protection, the protection of confidentiality, integrity, availability, and even a secure delivery state. In order to ensure a secure development process, these aspects must be taken into consideration above all during design, development, and manufacturing.