Industrial security


Cyberattacks pose a serious threat to individuals, companies, and government agencies
Cyberattacks as a top risk Cybersecurity is a decisive factor in the modern business world
The importance of cybersecurity has increased significantly in recent years. This is because the increase in cyberattacks is presenting major challenges for companies and public institutions. At the same time, increasing networking and digitalization means more points that are vulnerable to attack. In the European Union, for example, there is a ransomware attack every eleven seconds. And the attackers and attack methods are becoming more and more professional.
Implementing a comprehensive security strategy is essential to protect against ever-evolving threats and to prevent sabotage, downtimes, and data loss. Cybersecurity is a decisive factor in ensuring the operational capability of your company.

The implementation of cybersecurity measures is becoming law
Cybersecurity is becoming law The implementation of cybersecurity is no longer only mandatory for critical infrastructures
The digitalization of production, product, and customer data is one of the decisive factors for increasing the added value of a company. Therefore, this data must be given special protection.
The EU Commission recognized this and presented a European strategy for cybersecurity in December 2020. This defines standards for the security and defense capability of components, systems, and companies against cyberattacks. Legal requirements for the implementation of cybersecurity have long been established for critical infrastructures. This is now being extended with NIS 2, the new EU Network and Information Security Directive. However, the high requirements of the NIS 2 Directive can only be met if the products used have been developed in accordance with security-by-design. The Cyber Resilience Act (CRA) was defined by the EU to address this challenge. The new EU Machinery Regulation supplements the CRA, which also sees machines as a product.
Cybersecurity in industry
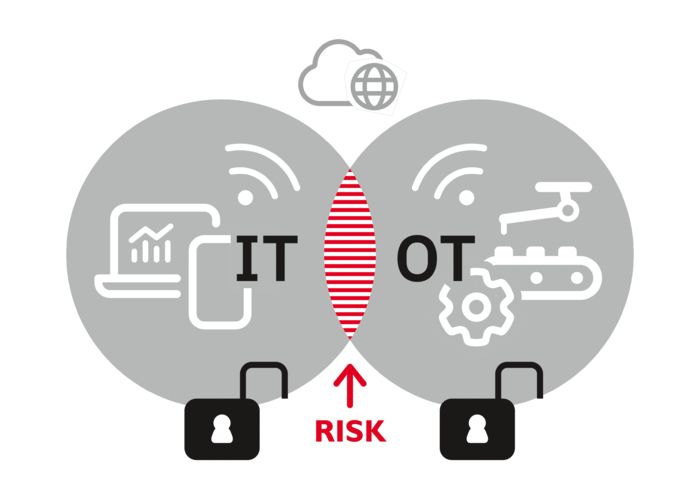
The requirements of ICS and IT security must be taken into consideration
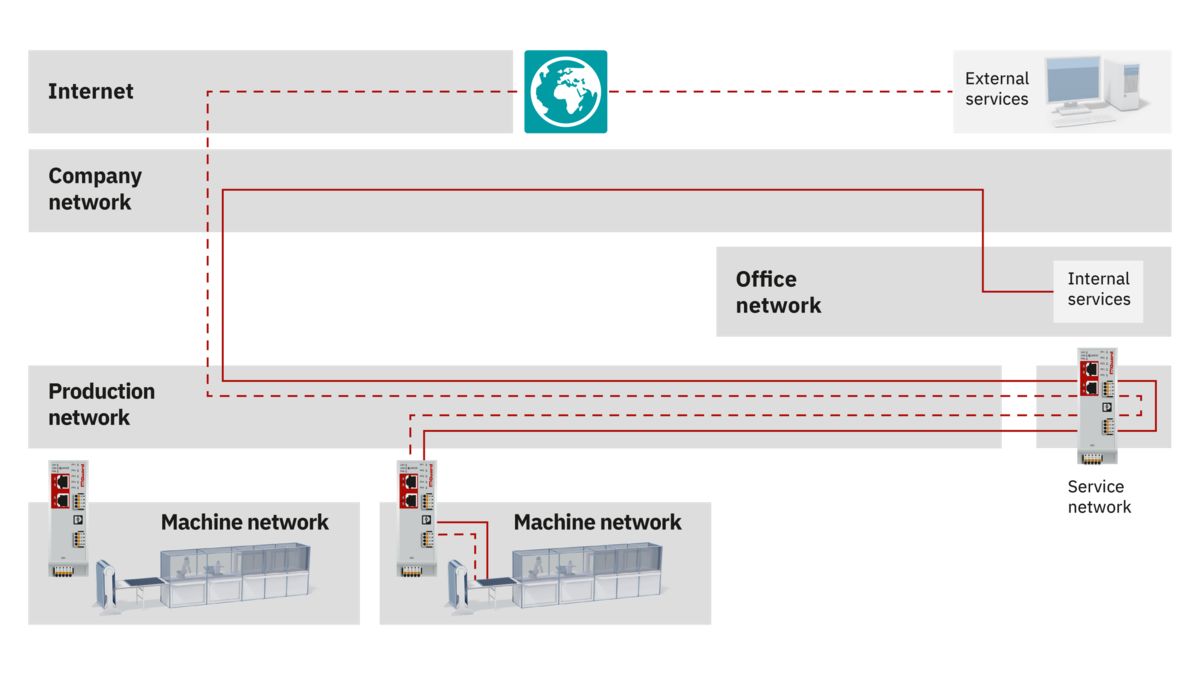
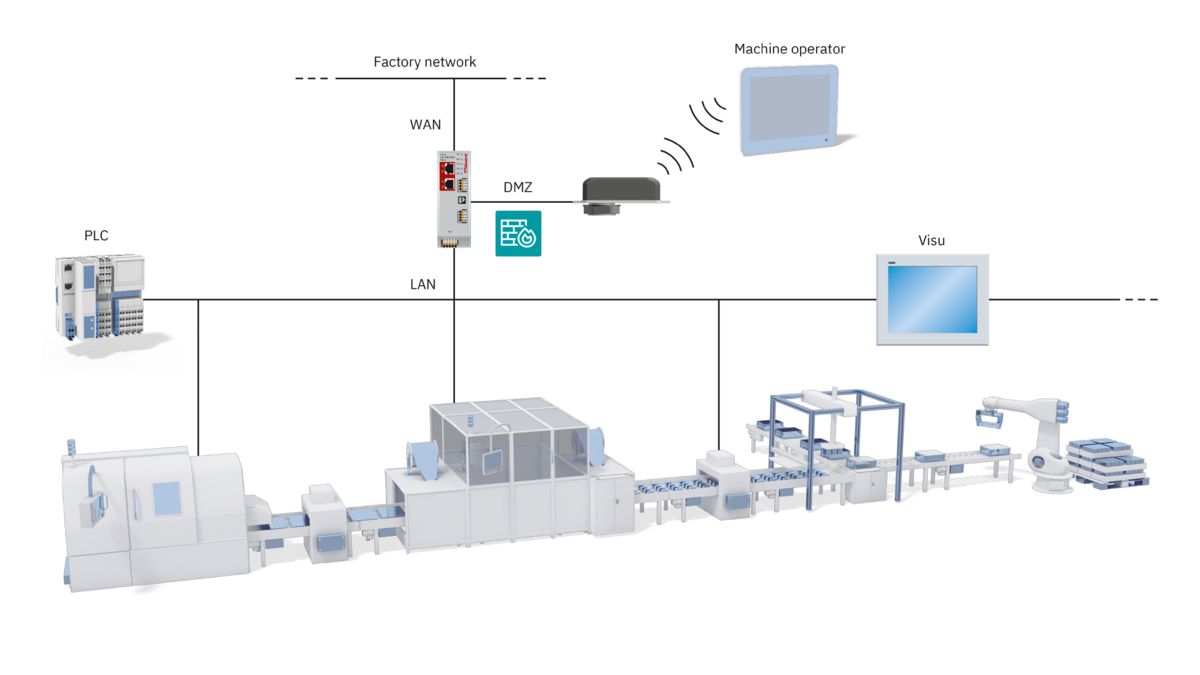
Combination of IT and OT
The security of your company is rooted in two different worlds: IT (information technology) and OT (operational technology). To properly protect your networks and systems, both worlds need to be considered and a comprehensive security concept is required. An effective and efficient approach can only be developed through coordinated action.
The IEC 62443 series of international standards aims to provide support for the secure operation of industrial automation systems (ICS systems), from design, through implementation, to management.
To this end, it sets out basic requirements for component manufacturers, system integrators, and operators. IEC 62443 builds on standard ISO 27001, which mainly consists of rules for IT security. Together, the two standards provide a holistic approach to protecting against cyberattacks.
The biggest cyber threats
The benefits of expanding networks, such as increased productivity or flexibility, are obvious. But increased networking and the resulting convergence of IT and OT mean that company networks have more points that are vulnerable to attack.
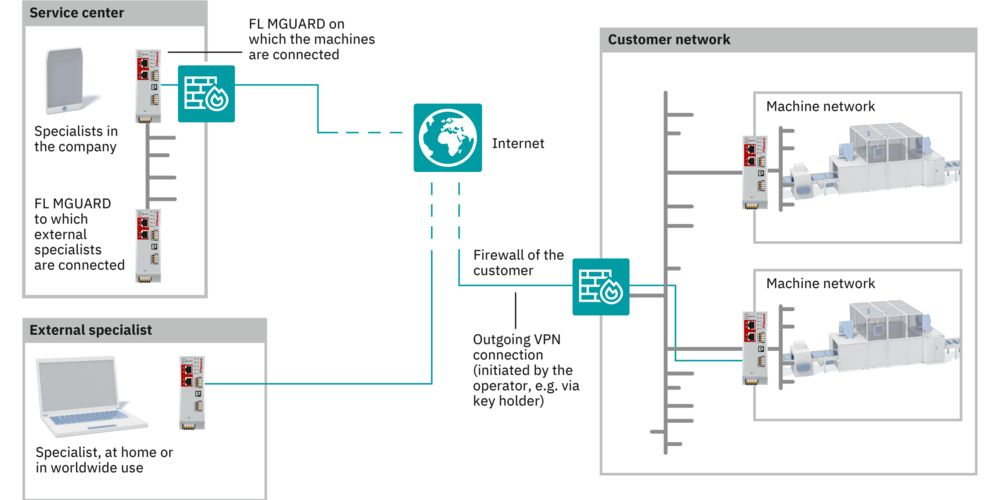
Criminals repeatedly succeed in exploiting potential vulnerabilities in the IIoT (Industrial Internet of Things) and thus gain access to companies and infrastructures. This raises the question of how large-scale automation environments can be networked while simultaneously ensuring that industrial systems are protected from hacker attacks and malware. The following points provide an overview of the biggest threats and possible precautionary measures.
Our cybersecurity concept
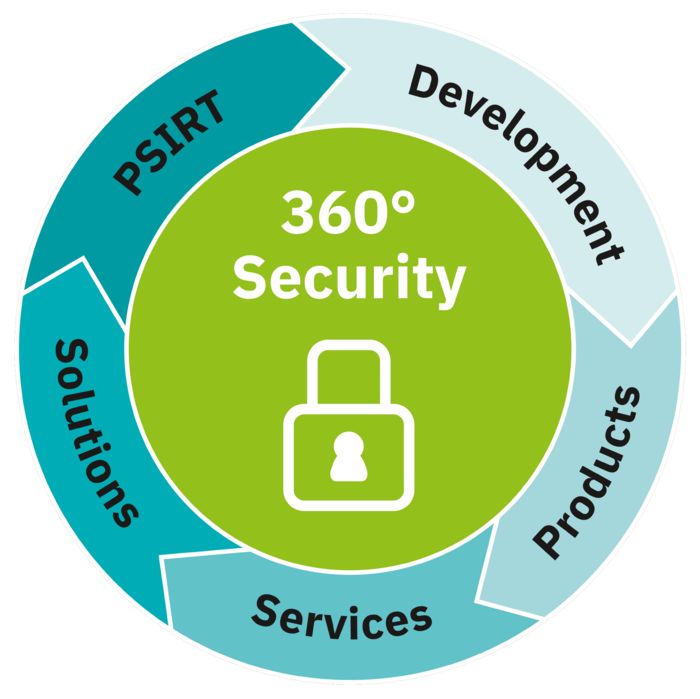
Our comprehensive 360° security concept
360° security – our comprehensive range without compromises
Good protection against cyberattacks can only be achieved if coordinated technical and organizational measures are intermeshed. We therefore provide 360° security, which simplifies the protection of systems and secures them from all sides:
Secure services
Our trained and expert security specialists provide consultation on how to minimize individual security risks in your plant and will develop a security concept (certified in accordance with IEC 62443-2-4) on request. We can share our knowledge with you in training courses to bring your employees up to speed on cybersecurity.
Secure solutions
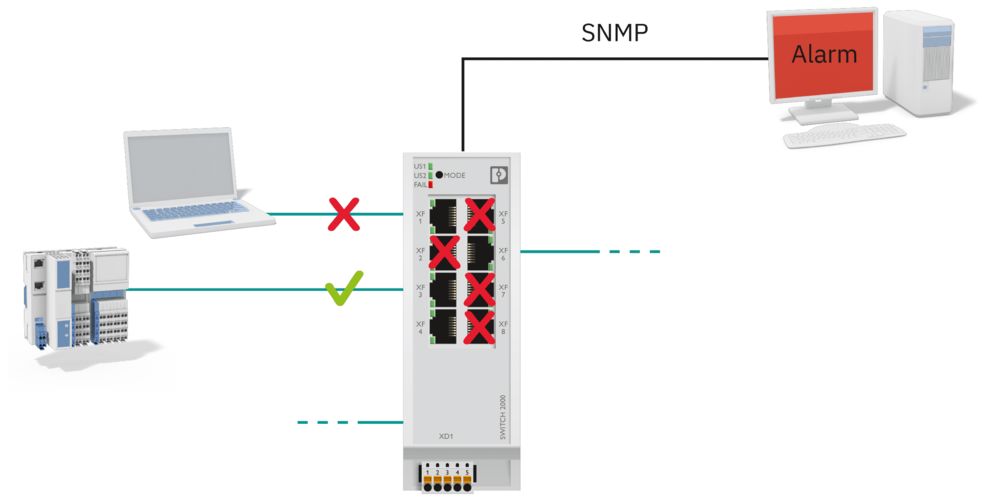
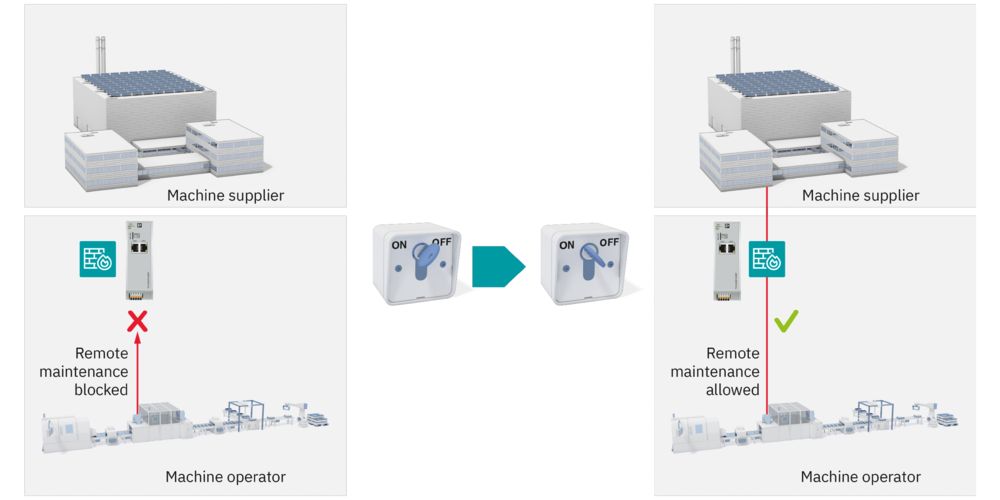
Our security concepts protect your critical processes, e.g., with the help of zone concepts, data flow control, and the use of hardened components. Secure processes are also established and documented.
Secure products
Security is firmly rooted in the entire life cycle of our products. Our products are developed in accordance with the IEC 62443-4-1 development process, and a two-digit number of devices are already certified in accordance with IEC 62443-4-2. In addition, our PSIRT, also certified in accordance with IEC 62443-4-1, provides additional security through transparent communication about security vulnerabilities and regular security updates.

LinkedIn: Industrial communication and cybersecurity Become a part of our community now!
Industrial communication networks enable us to reliably transmit data from the field, through the control level, all the way to the cloud. Our Industrial communication and cybersecurity LinkedIn page provides you with interesting information on network availability, cyber security, remote maintenance, and much more. Become a part of our community!