Cybersecurity podcast

Episode 1: Cybersecurity becomes law
The increasing digitalization in all areas makes the protection of data a central challenge. The EU Commission has also recognized this and has responded accordingly with the introduction of the NIS 2 Directive and the Cyber Resilience Act (CRA). The implementation of cybersecurity measures is legally binding. The NIS 2 security directive will become mandatory as early as October 18, 2024. The directive makes it obligatory for companies to substantiate their security strategy. In addition, binding requirements for products are defined within the CRA. The new EU Machinery Regulation also considers the aspect of cybersecurity in the context of functional safety.
There is therefore a lot to discuss in our first episode! Our expert, Andreas Fuß, explains the latest challenges, shares valuable tips, and provides a comprehensive assessment of the current schedule, which applies to the implementation of the new directives.
Guest: Andreas Fuß, Product Marketing Network Security
Further information on the new security directives:
Episode 3: Become a security expert
Cybersecurity is a dynamic and constantly growing subject area, as the threat landscape is constantly changing and cybercriminals are developing more and more professional methods of attack. It is therefore essential for security experts to stay up to date and be aware of current threats and defense strategies. There are many sources of information for this: specialist journals, social media channels, blogs, conferences, and webinars provide valuable information.
But how can you freshen up your specialist knowledge as effectively as possible? In the third episode of “Mission OT Security”, Hayley Lichtenfels provides an insight into her daily work. She herself works as a solutions architect and is aware of the current challenges.
Guest: Hayley Lichtenfels, Solutions Architect – Automation Infrastructure
Episode 4: Your guide to a security concept
We dive deep into the world of OT security in the fourth episode of Mission OT Security and show you how to create an effective security concept. What information is required, what are the most important requirements for a security concept, and what specific fields of action are there? We take a detailed look at how to realize a security concept.
Our expert, John Paul Morgan, Network Sales Engineer for Industrial Networks and Cybersecurity, is well versed in this. He examines the latest security status of the industrial network with customers, develops secure network concepts, and offers tailor-made training courses. Learn first-hand how you can protect your systems and facilities against cyberattacks.
Guest: John Paul Morgan, Network Sales Engineer – Industrial Networks and Cybersecurity
Further information on our range for industrial security
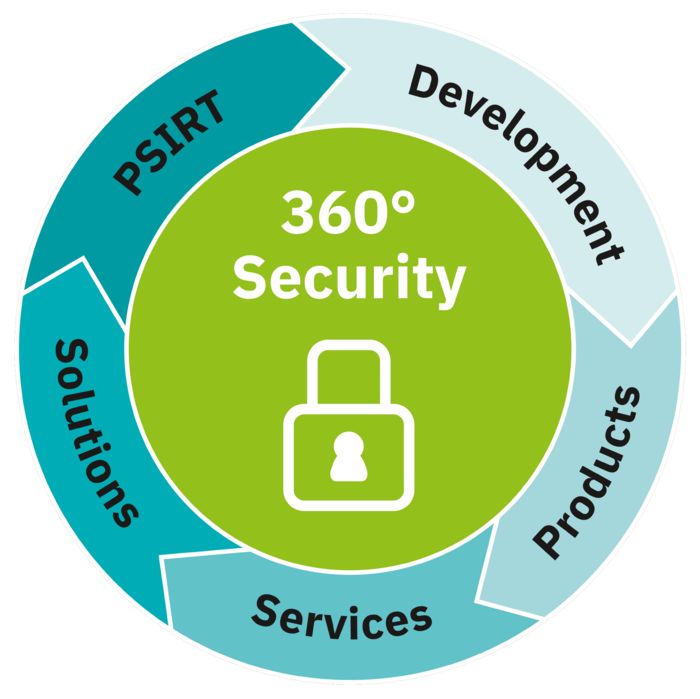
Our comprehensive 360° security concept
Our 360° security concept
Good protection against cyberattacks can only be achieved if coordinated technical and organizational measures are intermeshed. We therefore provide 360° security, which simplifies the protection of systems and secures them from all sides:
Secure services
Our trained and expert security specialists provide consultation on how to minimize individual security risks in your plant and will develop a security concept (certified in accordance with IEC 62443-2-4) on request. We can share our knowledge with you in training courses to bring your employees up to speed on cybersecurity.
Secure solutions
Our security concepts protect your critical processes, e.g., with the help of zone concepts, data flow control, and the use of hardened components. Secure processes are also established and documented.
Secure products
Security is rooted in the entire lifecycle of our products. It starts with a development process (certified in accordance with IEC 62443-4-1) and includes the integration of critical security functions and regular updates and security patches.
